Tomcat RCE via JSP Upload Bypass
CVE Dictionary Entry: CVE-2017-12617
NVD Published Date: 10/03/2017
NVD Last Modified: 04/23/2019
Current Description
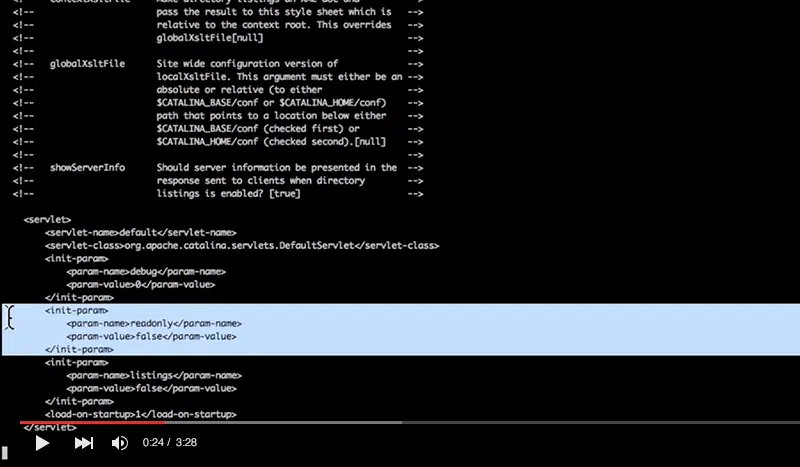
When running Apache Tomcat versions 9.0.0.M1 to 9.0.0, 8.5.0 to 8.5.22, 8.0.0.RC1 to 8.0.46 and 7.0.0 to 7.0.81 with HTTP PUTs enabled (e.g. via setting the readonly initialisation parameter of the Default servlet to false) it was possible to upload a JSP file to the server via a specially crafted request. This JSP could then be requested and any code it contained would be executed by the server.
Impact
CVSS v3.0 Severity and Metrics:
Base Score: 8.1 HIGH
Vector: AV:N/AC:H/PR:N/UI:N/S:U/C:H/I:H/A:H (V3 legend)
Impact Score: 5.9
Exploitability Score: 2.2
Attack Vector (AV): Network
Attack Complexity (AC): High
Privileges Required (PR):None
User Interaction (UI): None
Scope (S): Unchanged
Confidentiality (C): High
Integrity (I): High
Availability (A): High
CVSS v2.0 Severity and Metrics:
Base Score: 6.8 MEDIUM
Vector: (AV:N/AC:M/Au:N/C:P/I:P/A:P) (V2 legend)
Impact Subscore: 6.4
Exploitability Subscore: 8.6
Access Vector (AV): Network
Access Complexity (AC): Medium
Authentication (AU): None
Confidentiality (C): Partial
Integrity (I): Partial
Availability (A): Partial
Additional Information:
Allows unauthorized disclosure of information
Allows unauthorized modification
Allows disruption of service
Versions Effected
Tomcat 7.x
7.0.0, 7.0.1, 7.0.2, 7.0.3, 7.0.4 ,7.0.5, 7.0.6, 7.0.7, 7.0.8, 7.0.9, 7.0.10, 7.0.11, 7.0.12, 7.0.13, 7.0.14, 7.0.15, 7.0.16, 7.0.17, 7.0.18, 7.0.19, 7.0.20, 7.0.21, 7.0.22,7.0.23, 7.0.24, 7.0.25, 7.0.26, 7.0.27, 7.0.28, 7.0.29, 7.0.30, 7.0.31, 7.0.32, 7.0.33, 7.0.34, 7.0.35, 7.0.36, 7.0.37, 7.0.38, 7.0.39, 7.0.40, 7.0.41, 7.0.42, 7.0.43, 7.0.44, 7.0.45, 7.0.46, 7.0.47, 7.0.48, 7.0.49, 7.0.50, 7.0.51, 7.0.52, 7.0.53, 7.0.54, 7.0.55, 7.0.56, 7.0.57, 7.0.58, 7.0.59, 7.0.60, 7.0.61, 7.0.62, 7.0.63, 7.0.64, 7.0.65, 7.0.66, 7.0.67, 7.0.68, 7.0.69, 7.0.70, 7.0.71, 7.0.72, 7.0.73, 7.0.74, 7.0.75, 7.0.76, 7.0.77, 7.0.78, 7.0.79, 7.0.80, 7.0.81
Tomcat 8.0.x
8.0.0, 8.0.1, 8.0.2, 8.0.3, 8.0.4, 8.0.5, 8.0.6, 8.0.7, 8.0.8, 8.0.9, 8.0.10, 8.0.11, 8.0.12, 8.0.13, 8.0.14, 8.0.15, 8.0.16, 8.0.17, 8.0.18, 8.0.19, 8.0.20, 8.0.21, 8.0.2, 8.0.23, 8.0.24, 8.0.25, 8.0.26, 8.0.27, 8.0.28, 8.0.29, 8.0.30, 8.0.31, 8.0.32, 8.0.33, 8.0.34, 8.0.35, 8.0.36, 8.0.37, 8.0.38, 8.0.39, 8.0.40, 8.0.41, 8.0.42, 8.0.43, 8.0.45, 8.0.46
Tomcat 8.5.x
8.5.0, 8.5.1, 8.5.2, 8.5.3, 8.5.4, 8.5.5, 8.5.6, 8.5.7, 8.5.8, 8.5.9, 8.5.10, 8.5.11, 8.5.12, 8.5.13, 8.5.14, 8.5.15, 8.5.16, 8.5.17, 8.5.18, 8.5.19, 8.5.20, 8.5.21, 8.5.22
Tomcat 9.0.x
9.0.0.M1, 9.0.0.M2, 9.0.0.M3, 9.0.0.M4, 9.0.0.M5, 9.0.0.M6, 9.0.0.M7, 9.0.0.M8, 9.0.0.M9, 9.0.0.M10, 9.0.0.M11, 9.0.0.M12, 9.0.0.M13, 9.0.0.M14, 9.0.0.M15, 9.0.0.M16, 9.0.0.M17, 9.0.0.M18, 9.0.0.M19, 9.0.0.M20, 9.0.0.M21, 9.0.0.M22, 9.0.0.M23, 9.0.0.M24, 9.0.0.M25, 9.0.0.M26, 9.0.0.M27, 9.0.0
TomEE 1
1.5.2, 1.6.0.1, 1.6.0.2, 1.6.0, 1.7.0, 1.7.1, 1.7.2, 1.7.3, 1.7.4, 1.7.5
TomEE 7
7.0.0-M1, 7.0.0-M2, 7.0.0-M3, 7.0.0, 7.0.1, 7.0.2, 7.0.3, 7.0.4