Apache Tomcat CVE-2025-31650: The “Tomcat Killer” HTTP/2 Vulnerability
A newly published proof-of-concept (PoC) exploit for Apache Tomcat CVE-2025-31650 has transformed a previously known Apache Tomcat vulnerability into an active security threat. The flaw impacts how Apache Tomcat handles HTTP/2 requests, enabling unauthenticated attackers to exhaust server memory and trigger denial-of-service (DoS) conditions.
Apache Tomcat CVE-2025-31650 is rapidly gaining attention from attackers due to its low exploitation barrier and high impact across multiple Tomcat versions.
Warning: If you’re running Tomcat 8.5.x, 9.0.76–102, 10.1.10–10.1.39, or 11.0.0–11.0.5, your systems are vulnerable.
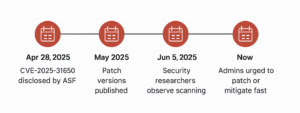
This issue has been monitored since late April, but the public release of a functional PoC in early June significantly lowered the exploitation barrier, making it accessible to less sophisticated attackers.
Active scanning activity has already been observed. Organizations using vulnerable Tomcat versions face elevated DoS risks. Fortunately, mitigation is both well-documented and straightforward. However, delays in patching can leave your systems exposed. See our Tomcat enterprise support services for expert mitigation guidance.
Apache Tomcat CVE-2025-31650 Affected Versions
| Tomcat Version | Status | Safe Upgrade |
|---|---|---|
| 8.5.x | ❌ Vulnerable (EOL) — Patched by Tomitribe | ➡️ Upgrade to 9.0.104+ |
| 9.0.76 – 9.0.102 | ❌ Vulnerable | ✅ Upgrade to 9.0.104 |
| 10.1.10 – 10.1.39 | ❌ Vulnerable | ✅ Upgrade to 10.1.40 |
| 11.0.0 – 11.0.5 | ❌ Vulnerable | ✅ Upgrade to 11.0.6 |
Apache TomEE Affected Versions
| TomEE Version | Embedded Tomcat Version | Status | Safe Upgrade |
|---|---|---|---|
| TomEE 9.x | Tomcat 10.1.10 – 10.1.39 | ❌ Vulnerable | ✅ Use TomEE 9.x with Tomcat 10.1.40+ |
| TomEE 8.x | Tomcat 9.0.76 – 9.0.102 | ❌ Vulnerable | ✅ Use TomEE 8.x with Tomcat 9.0.104+ |
| TomEE 7.x | Tomcat 8.5.x (EOL) | ❌ Vulnerable | ✅ Migrate to TomEE 8.x or 9.x with a supported Tomcat version |
Note: Tomcat 8.5.x has reached End-of-Life (EOL) and will not receive patches. TomEE 7.x users must upgrade to a supported version. Review Tomitribe’s Lifecycle Policy
Need support? Contact Tomitribe’s expert support team — we’re here to help.
Threat Timeline: CVE-2025-31650
Why Apache Tomcat CVE-2025-31650 Is a Critical Threat
HTTP/2 offers performance improvements like multiplexing and header compression — but its complexity introduces new attack surfaces. Apache Tomcat CVE-2025-31650 is a prime example of how these features can be misused to degrade server performance at scale.
What makes this HTTP/2 vulnerability in Apache Tomcat especially dangerous is:
- No authentication required — attackers don’t need credentials to launch the exploit.
- High automation potential — it can be scripted to affect thousands of servers at once.
- Already weaponized — a public PoC is circulating, and scanning activity has been observed.
- Hard to detect — the attack mimics valid HTTP/2 behavior, making it less obvious in logs or standard monitoring tools.
- Affects both Tomcat and TomEE — increasing its footprint across enterprise deployments.
Although mitigation is straightforward via patching or upgrading to a safe version, many organizations delay updates — often due to compatibility concerns or downtime risk. Unfortunately, that delay can leave production environments exposed to denial-of-service (DoS) attacks, service outages, and reputational damage.
Proactive patching and infrastructure hardening are your best defense — but knowing where to start can be challenging. Our Tomcat support subscription provides hands-on guidance, security expertise, and peace of mind. Whether you’re dealing with Apache Tomcat CVE-2025-31650 or planning long-term upgrades, our team ensures your systems stay protected and performant.
Apache Tomcat CVE-2025-31650 is a prime example of why expert support matters. Because of its unauthenticated nature, ease of exploitation, and public availability of attack code, it is considered one of the most severe Tomcat vulnerabilities in recent memory. Organizations should act now to ensure their systems are protected.
How Tomitribe Helps with Tomcat Security
Tomitribe partners with Fortune 500s, startups, and government organizations to secure and scale Apache Tomcat, TomEE and ActiveMQ Classic environments.
You’re not just getting support — you’re getting direct access to a team of project committers who contribute upstream code and patch critical vulnerabilities. Our senior engineers bring decades of combined experience securing and scaling large-scale Java server environments.
Here’s how we help organizations impacted by Apache Tomcat CVE-2025-31650:
- Support from project committers:
Get direct access to the apache committers and know the code inside and out. - 24×7 global coverage with 1-hour SLA:
We’re available via portal, phone, or email — any time, anywhere. - CVE mitigation & patching included:
Stay protected with proactive vulnerability tracking, expert guidance, and patched binaries for affected versions. - Simple core-based pricing:
Pricing is based on total cores where our binaries run, with automatic discounts at 64 (5%), 120 (7%), and 248 (10%) cores. - Professional services included at scale:
Unlock consulting and feature development at no extra cost once volume tiers are reached.
Looking for expert support? Reach out to us to discuss our annual Tomcat Enterprise Support contracts and get the help you need.